In the United States of America, cybersecurity breaches cost small businesses $34,600 annually. Everyone should know how to prevent cyber attacks. By implementing Security DevOps, you can prevent the financial losses that come with security attacks.
Dev Sec Ops equips businesses today to effectively deal with security issues. It incorporates your entire development process with solid security practices.
The Security DevOps pipelines are crucial aspects of the process. These ensure to keep your delivery processes consistent.
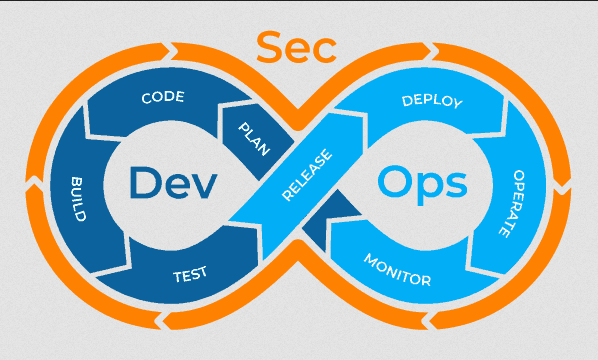
Security DevOps Pipelines
Security DevOps works to enhance security throughout your software and development process. The pipelines are a bunch of practices that incorporate security mechanisms into your process life cycle. They build, deploy, and test your software at a faster pace.
Advantages
DevSecOps pipelines provide the following advantages:
- Early detection of security breaches and vulnerabilities
- Enhances agility
- Secures the development process of your software
- Improves the recovery speed during security incidents
Phases of Security DevOps Pipelines
Security DevOps pipelines comprise different phases. Each phase requires the application of appropriate security checks.
The following are the phases of Security DevOps pipelines:
Plan
The planning stage requires the documentation of the product you are seeking to develop. It involves creating a task backlog in order of priority. Want to make a career in cybersecurity? It is crucial to identify and document the tasks that can support security functions and features. These can be encryptions or security checks.
You have to execute your security analysis. Additionally, create a plan that determines how, when, and where the regular security tests will occur.
You have to design threat modeling as well. It allows you to identify any subtasks that relate to security. The subtasks could include design adjustments or adding specific functionality.
Code
During this phase, you have to scan your codes. It involves analyzing the codes to ensure that they are free from vulnerabilities and bugs. Make sure to conduct both automated and manual reviews for better accuracy.
You can deploy Git controls and linting tools. This step helps you to secure your software and passwords. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools also help address bugs and security vulnerabilities early.
Build
At this phase, you build codes for execution. It becomes easier to track flaws before transferring them to production with SAST tools. These security tools will act specifically to the programming languages. Make sure that the code’s programming is compatible with the SAST tools you choose.
SAST tools also recommend solutions that you can use to resolve errors, bugs, or vulnerabilities. It allows you to deal with issues as soon as they appear effectively.
Test
For security testing at this stage, you can use DAST tools. They can scan your application in real-time. Any errors such as authorization and user authentication are instantly identified. If you want to know about Hamraaz Login, you must read it for army people.
You may also use exploratory testing such as penetration tests to verify security manually. It allows you to discover any weaknesses within the build.
Release
At this phase, you have to use security tools to analyze and scan for vulnerabilities. It is essential to do this just before you release the application.
Moreover, the build artifacts have to be signed. It verifies that the artifacts pass successfully. Then, you can store them in a secure registry.
Deploy
Once the above tests are complete in runtime, you have to secure the build for its final deployment to production. It is essential to test the integrity and security of the infrastructure and platforms.
Check if the network configurations, encryption keys, and security groups are the ones that you expect. A few post-deployment security tests can verify the success of the deployment.
DevSecOps maximizes your security. With the help of Security DevOps pipelines, you can identify vulnerabilities early. It allows you to resolve them swiftly before any considerable damage.